Tracking botnets, malicious users, worms and the like.
Summary:
Introduction:
(This project was done for the course of security in networks and computer systems, in the end of 2007 / beginning of 2008.)
Nowadays, SSH brute force attacks are common attack vectors not only by human people, but also for worms [1]. Preventing such a worm can be in part done by setting up a SSH setup that blocks for several seconds a brute force attack. Although the measures, and for some the risk, are well known, few servers apply them. Also, due to other hosts vulnerabilities our machine can suffer. SSH worms are also likely to use the known_hosts and stored public/private keys, as well as command history, to gain access to other machines. For one to be able to detect such a worm, specially when it’s not using its default brute-force attack vector, depends on knowing how it works. To help on this, and other problems (e.g. 0day exploits; unknown exploits;), a honeypot was devised. This honeypot should not throw off an experienced hacker, by behaving like a real machine, and by being stealthly monitored. In this work, we achieve and implement such an architecture. The monitoring and phorensic activities were left out of this work, but conditions for an essential part of those to happen have been devised.
Architecture:
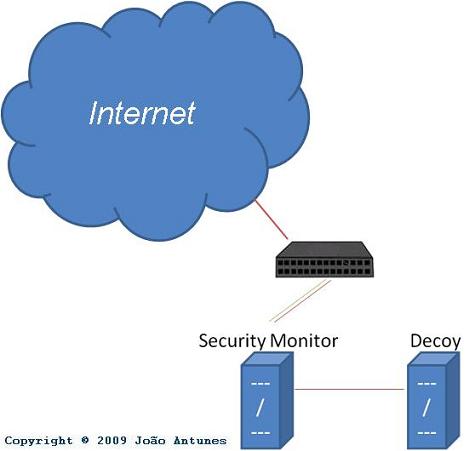
The idea behind this project is to allow an attacker to gain access to a decoy operating system. Afterwards, the decoy locks down, i.e. it won’t allow more attackers, thus allowing only one attacker at a time. The attacker’s newly created username/password is stored and sent back to the Security Monitor via a very stealth ICMP Echo reply payload as well as the active SSH session keys used by the sshd server.
After being transmitted the username, password, and session keys, another passive machine, the SecurityMonitor, is able to monitor the communication between the decoy and the rest of the world, unencrypted, thus monitoring the attacker’s activities!
Technologies/tools used:
– VMWare;
– Kernel Module to provide stealth monitoring inspired on http://www.phrack.org/issues.html?issue=61&id=13#article ;
– SSH source code meddling;
– Wireshark sniffer;
The decoy is rigged: it’s sshd daemon (whose code has been altered) allows bruteforce attacks to succeed. After n random attempts, an attacker is automatically in, its user and password are used to create the new user and the sshd stops letting in attackers, while allowing the kernel module to leak SSH’s session password through a stealth network channel (ICMP payload XORed with a pre-determined password).
Interested? want to know more, get the sources, etc? contact me
—

All of the projects published here by João Antunes are licensed under a Creative Commons Attribution-Noncommercial 3.0 United States License.
Permissions beyond the scope of this license may be available here.